Forty unlocked doors: Hidden compliance risks in every cloud

Between January 1st and June 30th 2025, Unosecur analysts scanned 50 multi‑cloud environments for cloud compliance gaps tied to identity and access management (IAM). The sample covered AWS, Azure, and Google Cloud estates across finance, healthcare, manufacturing, and SaaS sectors.
Key metric: The team logged an average of 40 identity‑related control failures per cloud tenant. These were not some sophisticated exploits unearthed by deep research, but everyday hygiene misses.
Privileged accounts without MFA; duplicate machine keys; over‑broad roles; stuff that auditors flag and attackers love.
Why forty identity gaps matter
- Audit exposure: Forty open items translate into forty findings on an ISO 27001, SOC 2, or PCI‑DSS worksheet. In our data set ISO 27001 clause 5.17 (privileged MFA) was violated by 68 % of companies.
- Predictable breaches: Ransomware crews prey on routine weaknesses. Our incident library shows two‑thirds of 2025 identity‑driven breaches began with one of the four gap families detailed below.
- Insurance penalties: Cyber‑insurers now ask for proof that keys rotate every 30 days and that standing admin roles are eliminated. Miss the basics and premiums spike, after a breach they spike twice.
Four common cloud access failures
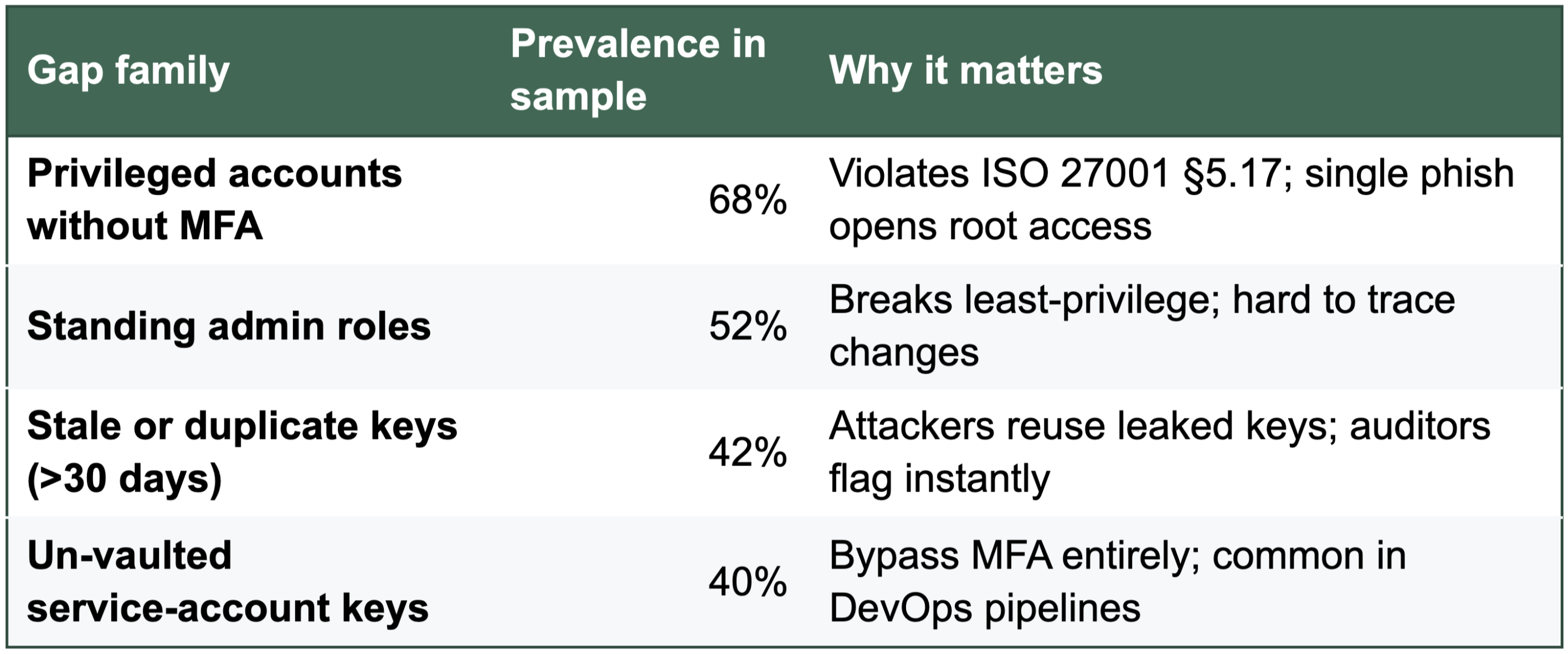
Together these four issues created 70 % of all high‑severity findings in the benchmark.
Impact on audits, insurance, and breaches
- Audit fatigue: Teams spent an extra 26 hours on average gathering evidence for every 10 unresolved findings.
- Premium hikes: Firms with more than 25 unresolved access gaps paid 18 % higher cyber‑insurance rates at renewal.
- Real‑world breaches: Ransomware groups increasingly weaponise service‑account keys within hours of discovery. Every leaked key is effectively an unlocked door.
Three‑step fix for cloud compliance
- Count your own doors – Run an automated baseline scan that maps directly to ISO 27001, PCI‑DSS v4, and SOC 2 IAM controls.
- Close the obvious ones first – Enforce IdP‑based MFA on every privileged account, remove always‑on admin roles, and vault or rotate keys older than 30 days.
- Measure, don’t guess – Track four identity KPIs monthly: Privileged MFA %, Standing Admin Roles, Stale Keys, Vaulted Service‑Account Keys.
The bottom line for CISOs
Attackers do not care how many AI agents, containers, or micro‑services you run; they look for the simplest unlocked door. Our Cloud Compliance Pulse H1 2025 proves that the doors are still wide open, forty on average. Close them now, before an auditor or attacker walks right in.
Next week we’ll release the full H1 2025 Cloud Compliance Pulse, breaking down the data by provider, sector, and region. Until then, how many unlocked doors do you think your own tenant is hiding?
Don’t let hidden identities cost you millions
Discover and lock down human & NHI risks at scale—powered by AI, zero breaches.