OWASP Top 10 for Non-Human Identities (NHI): Why Securing Machine Identities Is Now Mission-Critical
Modern infrastructure doesn’t rely on humans anymore it runs on machines. Service accounts, API keys, OAuth apps, bots, cloud roles, and workload identities quietly keep the digital world humming in the background. These Non-Human Identities (NHIs) now outnumber human users by staggering margins. They deploy code, run CI/CD pipelines, move data between clouds, coordinate microservices, and authenticate to every critical system behind the scenes. Yet while organizations have invested heavily in securing human identities through MFA, SSO, and behavioral analytics, the vast population of machine identities often remains unmanaged, unmonitored, and poorly understood. This silent sprawl has become one of the most strategic gaps in modern cybersecurity. The OWASP NHI Top 10 (2025 Initial Edition) steps directly into this gap. It provides the first structured, vendor-neutral framework dedicated to the security failures and risks tied to machine identities. Far from being an academic exercise, this work highlights real-world incidents of breaches that occurred because a forgotten test account, leaked API key, or overprivileged OAuth app opened the door.
At Unosecur, we’ve long believed that identity is the true control plane of the cloud. That belief makes the OWASP NHI Top 10 more than just a guide for us; it validates the urgency we see every day across customer environments. As enterprises expand their automation footprint, identities become the ultimate perimeter.
This blog breaks down OWASP’s NHI Top 10, contextualizes the real-world incidents behind each risk, and shows how organizations can build machine identity resilience at scale.
Why NHIs Matter More Than Ever
Automation reshaped the risk landscape long before many security teams had the visibility to understand it. Microservices authenticate thousands of times per minute, CI/CD systems deploy code across regions automatically, and SaaS-to-cloud connections rely heavily on long-lived tokens that rarely see governance. All of this means that the most privileged entities in modern environments are no longer humans, they're machines. This shift brings a new class of threats that are faster, harder to detect, and extremely powerful when exploited.
Three themes define this transformation:
1. From Human to Machine
Machine identities perform tasks that once required human admin credentials. Their privileges often exceed human access, and they rarely use MFA or conditional access.
2. Visibility → Automation → Governance
OWASP’s model hinges on a simple truth: without visibility, you cannot enforce automation; without automation, you cannot enforce governance. Most organizations don't know how many machine identities they have, let alone what they do.
3. New Threats, Faster Attacks
Machine identities are constantly authenticated. A single leaked token can trigger cloud-wide access in seconds, not hours. Attackers know this and target NHIs accordingly.
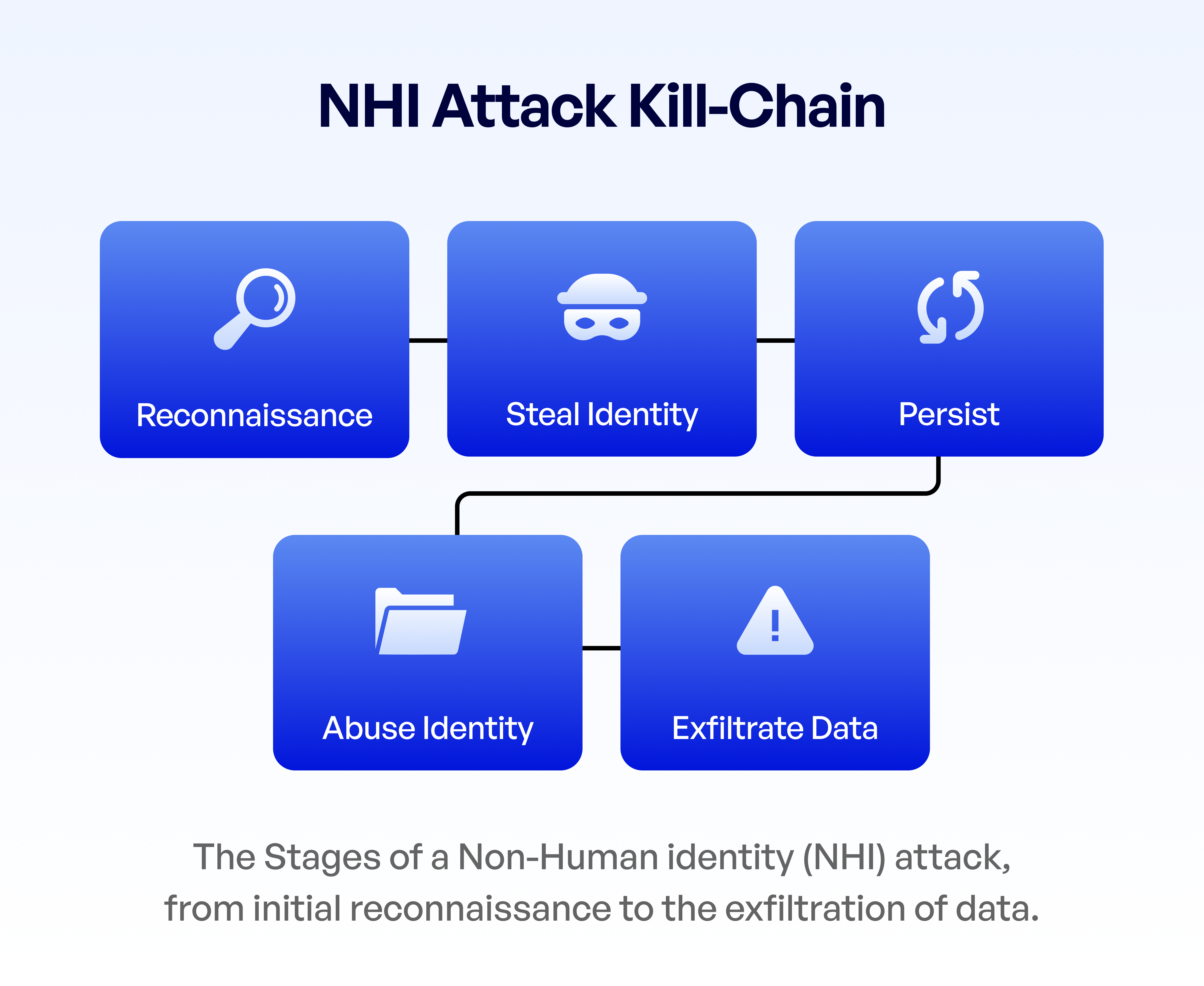
The OWASP Top 10 for Non-Human Identities (NHI)
What follows is a streamlined and publication-ready breakdown of the OWASP NHI Top 10 risks, enriched with context and real-world examples that show just how common and dangerous these failures are.
NHI1:2025 – Improper Offboarding
Stale service accounts, forgotten API keys, and orphaned OAuth apps become long-term attack footholds when they’re left active. Because they often carry broad access and are rarely monitored, they offer attackers persistent entry into critical systems.
Improper offboarding typically happens quietly: an engineer leaves the company, a microservice is deprecated, or a test environment is shut down, but the underlying identity remains. Over time, these identities accumulate risk, waiting for the wrong actor to discover them.
Real incident:
Midnight Blizzard (NOBELIUM), 2024: Microsoft revealed that attackers compromised a legacy test account lacking MFA, pivoted to a legacy OAuth app, and gained full programmatic access to internal mailboxes.
NHI2:2025 – Secret Leakage
Secrets leaking into public repositories, mobile applications, logs, or CI/CD configs remain one of the fastest paths to compromise. Machine credentials are often treated as “implementation details,” leading to careless storage and reuse.
Even a single leaked API key can grant attackers full impersonation capability.
Real incident:
Tata Motors, 2025: Hardcoded AWS keys and API tokens embedded in public applications exposed over 70 TB of sensitive data.
NHI3:2025 – Vulnerable Third-Party NHIs
Organizations rely heavily on SaaS tools, BI platforms, and third-party automations. But every third-party integration introduces identities that the organization doesn’t fully control and often doesn’t monitor.
A single compromised vendor becomes a multi-organization breach.
Real incident:
Sisense, 2024: Attackers accessed customer data connection strings and cloud tokens through a compromise of Sisense’s internal systems.
NHI4:2025 – Insecure Authentication
Legacy authentication patterns like static API keys, implicit OAuth flows, or long-lived SAS tokens continue to underpin critical workflows. These outdated mechanisms lack MFA, fail to enforce token binding, and create trivial replay opportunities for attackers.
Real incident:
Microsoft SAS Token Exposure, 2023: An overly privileged, unexpired SAS token was accidentally published, enabling unauthorized access to Azure Storage.
NHI5:2025 – Overprivileged NHI
Machine identities often receive broad or administrative permissions “just to make things work.” Over time, these permissions remain unreviewed, leading to massive blast radius potential when compromised.
Real incident:
CircleCI Breach, 2023: An overprivileged OAuth token allowed attackers to exfiltrate customer secrets stored within CI/CD workflows.
NHI6:2025 – Insecure Cloud Deployment Configurations
CI/CD pipelines frequently rely on static credentials, misconfigured OIDC trust rules, or permissive IAM roles. These pipelines sit at the heart of software supply chains, making them high-value targets.
Real incident:
GitHub OIDC → AWS Misconfiguration, 2024: Organizations trusting GitHub’s OIDC provider without restricting the sub claim inadvertently allowed unauthorized repositories to assume privileged AWS roles.
NHI7:2025 – Long-Lived Secrets
Long-lived keys are effectively permanent entry passes. When exposed, they enable persistent, undetectable access that blends into normal machine traffic.
Real incident:
Snowflake Customer Breach, 2024: Attackers used year-old static API keys harvested from infected developer machines to access and exfiltrate customer datasets.
NHI8:2025 – Environment Isolation Failures
When a test or development NHI works in production, the entire boundary between low-security and high-security environments collapses. Attackers simply compromise the weakest environment and walk upward.
Real incident:
Azure Managed Identity Cross-Environment Exposure, 2024: Shared managed identities across dev and prod subscriptions enabled potential pivot paths into production workloads.
NHI9:2025 – NHI Reuse
Reusing the same service account or API key across multiple workloads causes identity sprawl and makes rotation risky or disruptive. It also blurs attribution, complicating detection and response.
Real incident:
Google Chronicle, 2023: Misconfigured backend service accounts accessed multiple tenant environments due to NHI reuse.
NHI10:2025 – Human Use of NHIs
When developers manually use machine identities for debugging or burndown tasks, they bypass MFA, break audit logs, and create untraceable access paths.
Real incident:
CircleCI, 2023: A developer’s manual use of a machine token enabled attackers to impersonate automation processes and exfiltrate customer secrets.
Structural Challenges the OWASP NHI Top 10 Exposes
NHIs reveal deeper architectural weaknesses across the modern enterprise. At scale, the problems are not just identity by identity; they're systemic.
The Visibility Vacuum:
Organizations cannot secure what they cannot see. NHIs spread across clouds, CI/CD, and SaaS platforms often go unnoticed.
Fragmented Management:
Secrets live in vaults, cloud IAM, GitHub, and pipelines, but no single system owns them.
Hidden Trust Chains:
APIs talk to APIs that talk to pipelines that talk to cloud roles. These silent dependencies create cascading risk.
Human Oversight Gaps:
Developers create long-lived tokens, skip rotation, and leave service accounts behind.
No Perimeter, Only Identities:
In a distributed cloud world, identity, not IP address, is the new perimeter.
How Unosecur Turns the OWASP NHI Framework Into Action
The OWASP NHI Top 10 is a map. Unosecur provides the vehicle to act on it.
A Unified NHI & Secret Inventory:
Every machine identity across AWS, Azure, GCP, and SaaS is automatically discovered and correlated.
Automated Lifecycle Governance:
Offboarding, rotation, expiry, and ownership assignment are done with no-code automation.
Behavior-Based ITDR:
Unosecur detects machine impersonation, privilege escalation, dormant key activation, and unusual cross-environment activity using real-time identity analytics.
Shift Left for Developers:
Risk is caught in CI/CD before insecure identities ever touch production.
Benchmarking Against OWASP NHI:
Continuous scoring, drift detection, and audit-ready reports bring measurable identity resilience.
Conclusion: Securing the Machine Perimeter
Machine identities now form the backbone of the digital world. They deploy, authenticate, orchestrate, and connect every piece of modern infrastructure. As this machine-to-machine ecosystem grows, so does the opportunity for attackers to exploit trust relationships that were never designed with scale or security in mind. The OWASP NHI Top 10 is a wake-up call for the industry. It challenges organizations to rethink identity security from the ground up and treat machine identities with the same rigor once reserved for human accounts. Unosecur is built for this new reality. By providing deep visibility, automated governance, and continuous threat detection for every NHI across cloud and SaaS environments, Unosecur helps organizations build identity systems that are resilient, auditable, and secure by design.
In a world where machines outnumber humans in your environment, the path to resilience is clear: secure every identity, everywhere, because the perimeter is no longer a place; it’s an identity.
Don’t let hidden identities cost you millions
Discover and lock down human & NHI risks at scale—powered by AI, zero breaches.



