Identity-Driven Intrusion Validation: How to prove real identity abuse

TL;DR - Identity-Driven Intrusion Validation: How to Prove Real Identity Abuse
From infostealers to intrusion:
The Jaguar Land Rover (JLR) breach highlights how attackers harvest credentials through infostealers and later use them to log in as trusted users, bypassing malware detection and appearing legitimate.
Why IDIV matters:
Identity-Driven Intrusion Validation (IDIV) verifies whether stolen or misused identities were actually used to infiltrate systems, connecting credential exposure to operational compromise through evidence-based forensics.
How it works:
IDIV correlates logs across endpoints, identity providers, cloud platforms, and SaaS apps to build a verifiable timeline of exposure → reuse → action → impact, revealing how identity misuse unfolds in real time.
Where Unosecur fits in:
Unosecur automates the entire IDIV process. Its Unified Identity Fabric, ITDR, and ISPM modules detect credential reuse, reconstruct attacker activity, and enable one-click containment, turning identity forensics into a proactive defense aligned with MITRE ATT&CK T1078, NIST SP 800-61 Rev. 3, and CISA ZTMM v2.0.
JLR data breach and the infostealer connection
A common thread ran among all the detailed analysis and studies of the Jaguar Land Rover (JLR) data breach: infostealers managed to harvest the company credentials long ago, and this is the most likely cause for the breach.
Imagine an employee or vendor unknowingly infected with an infostealer, a lightweight malware designed to harvest browser cookies, session tokens, and saved passwords. Those stolen artifacts are quietly sold or shared on dark-web forums, exposing credentials tied to internal systems, cloud apps, or supplier portals.
This is where the first domino falls: the exposure of real, usable identities. An attacker armed with those credentials doesn’t need exploits or zero-days. By replaying stolen sessions or logging in through legitimate interfaces, they appear as authorized users. Once inside, they can escalate privileges, assume cloud roles, or access sensitive repositories like design files and supplier databases.
As evident in the MITRE ATT&CK analysis of the JLR cyberattack, every step blends into normal user behavior, leaving traditional endpoint detection tools blind because no malicious payloads are dropped, just valid logins performed for malicious ends. It underlines the need for Identity-Driven Intrusion Validation (IDIV). The majority of modern breaches now begin valid credentials, often stolen through phishing, infostealers, or supply-chain compromise. Traditional forensics tools can miss these attacks completely. Identity-Driven Intrusion Validation (IDIV) fills that gap.
What Is Identity-Driven Intrusion Validation (IDIV)?
IDIV is a forensic framework that verifies whether attackers used real accounts (credentials, tokens, API keys, or service accounts) to infiltrate systems or move laterally inside them. It connects two ends of the intrusion chain: credential exposure (how attackers got valid identities) and operational compromise (what they did afterward).
In a classic malware-based attack, analysts find payloads or persistence artifacts. In identity-driven intrusions, there’s no malware to trace: only authentication events and privilege changes. That’s why IDIV focuses on correlating identity evidence instead of code signatures. It proves, with evidence, whether a stolen or misused identity actually enabled an intrusion, and shows exactly how it happened.
Core components of IDIV
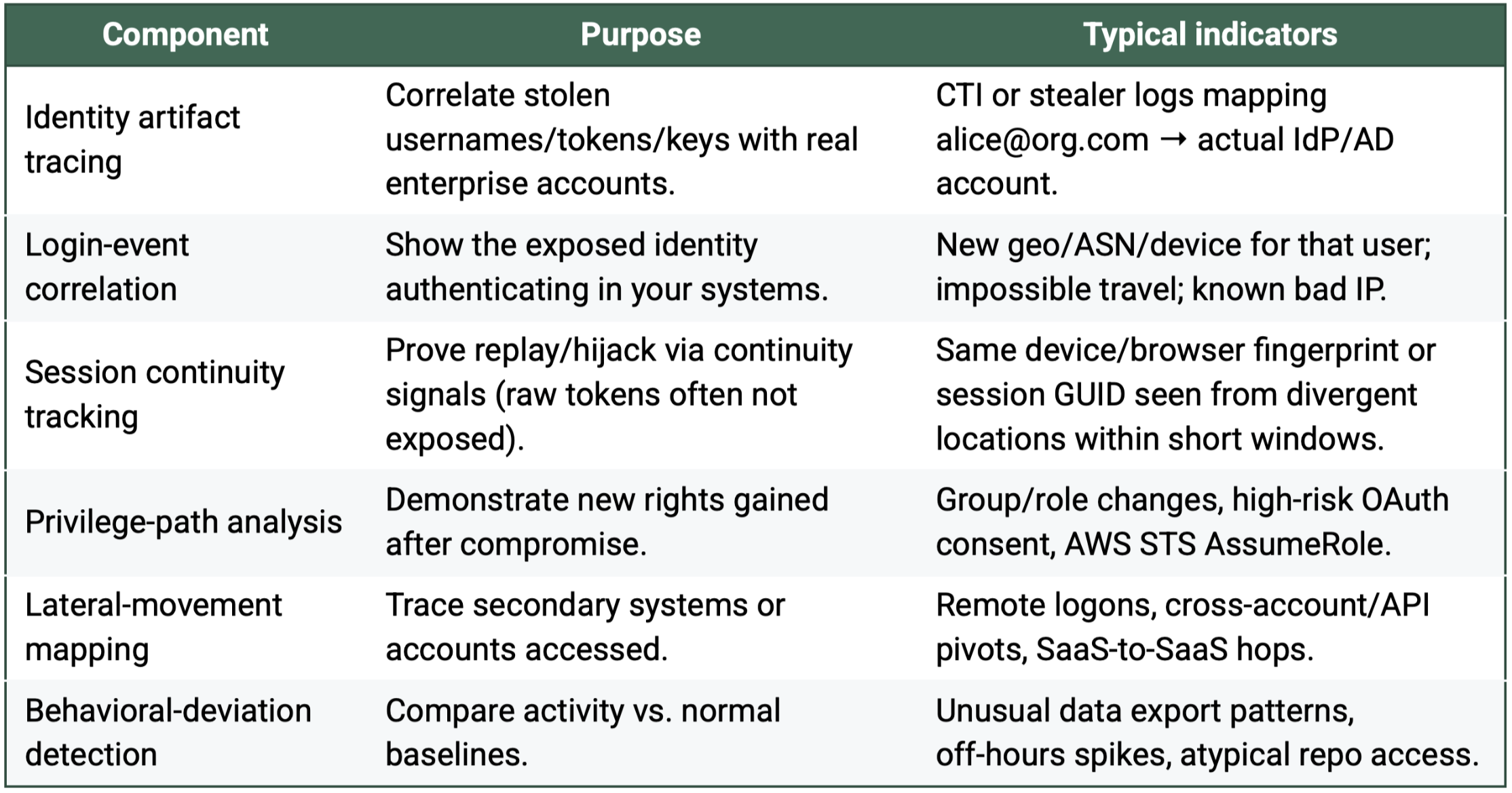
Why identity validation is now essential
Between 2024 and 2025, identity abuse became one of the dominant attack vectors across industries. Identity compromise accounted for 35% of all cloud intrusions in the first half of 2024; Stolen credentials was the initial vector in roughly 16% of investigated cases in 2024. Microsoft’s 2024 Digital Defense Report recorded an average of 7,000 password-based attacks per second.
Traditional detection methods fail because no malicious payloads are dropped, and system-integrity tools see a “clean” endpoint. IDIV shifts analysis to the identity layer, correlating leaked credentials with authentication, session activity, and privilege escalation to reveal the real breach path.
How IDIV works in practice

An IDIV investigation moves through four verifiable stages that build an evidence chain from exposure to impact.
- Exposure: Prove that a credential, token, or key was compromised, through stealer logs, breach repositories, or CTI data.
- Reuse: Show that the same identity authenticated into your environment. Device fingerprints, IP patterns, or session GUIDs create correlation stronger than usernames alone.
- Action: Identify what happened under that identity: file downloads, privilege escalation, API calls, or lateral connections.
- Impact: Link those actions to real consequences such as exfiltration, downtime, or tampered logs.
When these steps align chronologically, you can confirm an identity-driven intrusion, not just credential reuse. This approach directly aligns with MITRE ATT&CK T1078 (Valid Accounts), which maps how adversaries exploit legitimate access.
Here are the signals you need to track
An IDIV workflow draws on multiple telemetry layers, each offering a fragment of truth:
- Endpoint data (EDR/XDR): Reveals infostealer activity or credential harvesting.
- Identity providers (IdP): Authentication logs from Microsoft Entra ID, Okta, or Ping Identity show login anomalies and privilege changes.
- Cloud platforms: AWS CloudTrail, Azure Activity Logs, and GCP Audit Logs expose role assumptions, key usage, and cross-account actions.
- Network telemetry: VPN and NetFlow records validate session origin, geolocation, and egress volumes.
- SaaS applications: GitHub, Jira, Salesforce, and Slack audit logs highlight risky OAuth grants or unexpected admin actions.
- Threat-intelligence sources: Commercial CTI feeds and dark-web repositories confirm whether credentials appeared publicly before being reused.
The strength of IDIV lies in correlating these diverse signals over time to reconstruct the attacker’s true path through the environment. When executed correctly, IDIV produces tangible, actionable outcomes:
- A verified timeline connecting identity exposure to system compromise.
- Attribution mapping that links stolen identities or tokens to attacker infrastructure.
- Containment actions that revoke sessions, disable accounts, rotate keys, and remove risky OAuth consents.
- Control feedback showing exactly where defenses failed: missing MFA coverage, stale service accounts, or unrestricted admin roles.
Integrating IDIV Into SOC and DFIR workflows
IDIV becomes most effective when built into day-to-day security operations.
Tier 1 SOC analysts monitor identity anomalies: unusual MFA prompts, impossible-travel logins, or rapid privilege escalation. Tier 2 analysts correlate those anomalies with threat-intelligence evidence to verify exposure.
Incident-response teams reconstruct the full chain of events, while threat-hunting teams proactively look for dormant identity reuse that escaped initial detection. IAM and GRC teams then turn these lessons into preventive controls: stronger conditional access, Just-In-Time privileges, and automated token rotation. This is where Unosecur changes the game.
How Unosecur enhances your IDIV workflow
Built around its Unified Identity Fabric (UIF), Identity Threat Detection and Response (ITDR), and Identity Security Posture Management (ISPM) modules, Unosecur delivers end-to-end visibility across every identity: human, machine, or service. The platform automatically correlates leaked or stolen credentials discovered in external threat-intelligence feeds with real accounts inside Entra ID, Okta, AWS IAM, and SaaS systems. By doing so, it provides the first and most critical element of IDIV: establishing that an exposed identity belongs to a live, active account inside your environment.
Once correlation is established, Unosecur detects and validates real-world reuse. Its ITDR continuously monitors identity activity across cloud, SaaS, and on-prem systems, flagging suspicious patterns such as token replay, concurrent logins from multiple regions, or session anomalies that indicate an attacker logging in with stolen credentials. Going beyond detection, Unosecur’s real-time analytics trace how that compromised identity moves, whether privileges were elevated through role assumptions or lateral access, and which systems were touched. This effectively reconstructs the “action” phase of the IDIV chain with precision.
If the investigation confirms compromise, Unosecur automates containment. Its Unified Identity Fabric allows analysts to revoke sessions, roll back privileges, invalidate access tokens, and rotate keys in seconds. What once required manual, error-prone steps across different cloud consoles now happens from one unified pane of glass. And as incidents close, Unosecur’s ISPM engine feeds every insight back into posture improvement, quantifying MFA coverage, token hygiene, and admin exposure to strengthen future prevention.
With Unosecur, IDIV shifts from a labor-intensive forensic exercise to a continuous, intelligence-driven capability. It doesn’t just prove how attackers used valid identities; it stops them in real time and ensures the organization learns from every attempt. By aligning with frameworks such as MITRE ATT&CK T1078, NIST SP 800-61 Rev 3, and CISA’s Zero Trust Maturity Model v2.0, Unosecur turns identity forensics into a living, automated defense system, delivering proof, protection, and posture in one motion.
Don’t let hidden identities cost you millions
Discover and lock down human & NHI risks at scale—powered by AI, zero breaches.



