Third‑party cybersecurity risks at the aviation sector: Lessons from Qantas 2025 data breach

The Qantas 2025 data breach incident underscores how the aviation sector’s sprawling vendor ecosystem can expose carriers to unseen third‑party risks.
In late June 2025, attackers linked to Scattered Spider, an aggressive APT group, slipped through an offshore contact‑centre platform rather than Qantas’ own network, reminding airlines that supplier security can become the weakest link.
TL;DR
- Social‑engineering breach of an offshore customer‑service platform allowed unauthorized access to personal data of up to 6 million Qantas customers, bypassing the airline’s internal defenses.
- Indicators and FBI/CISA alerts point to Scattered Spider, known for impersonating staff, defeating MFA, and pivoting through third‑party systems across airline supply chains.
- Although core operations stayed online, the breach triggered legal action, reputational damage, and board‑level scrutiny, showing aviation companies must treat vendor security as integral to their own attack surface and move beyond “checkbox” compliance to continuous third‑party oversight.
- The aviation sector is no longer just about logistics. Airlines and similar enterprises are fundamentally digital businesses. Security must be embedded in every business process and relationship, not bolted on as an afterthought
How a third‑party contact‑centre became Qantas’ weakest link
On 30 June 2025, Qantas detected “unusual activity” on a third-party customer service platform used by one of its offshore contact centres, which led to unauthorized access to personal data of up to 5.7–6 million customers. “The incident occurred when a cyber criminal targeted one of our airline contact centres and gained access to a third-party customer servicing platform,” said a Qantas statement on July 2.
External sources, including the BBC, cybersecurity analysts, and the FBI, have attributed similar attacks in the airline sector to a cyber criminal group known as Scattered Spider.
Scattered Spider: Tactics and targets of the airline‑focused APT group
“The attack comes just days after the FBI issued an alert... warning that the airline sector was a target of cyber criminal group Scattered Spider,” said the BBC report.
According to the cybersecurity advisory by CISA, USA, Scattered Spider is known for:
- Using social engineering and identity spoofing.
- Impersonating staff or IT personnel to gain access to remote platforms, including helpdesks and admin panels.
- Moving laterally within third-party systems to extract bulk PII.
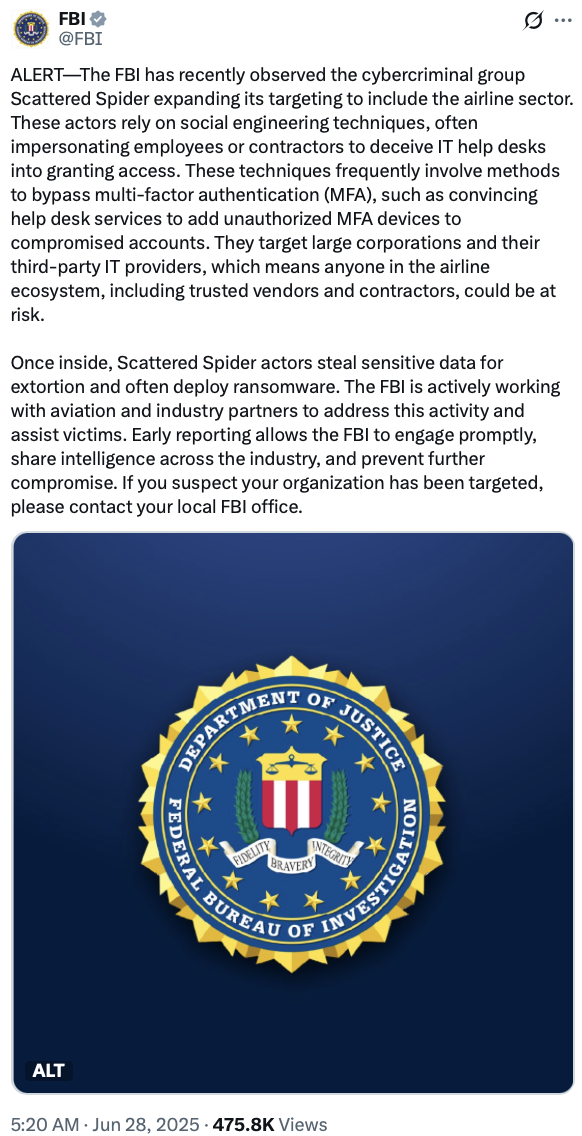
“These techniques frequently involve methods to bypass multi-factor authentication (MFA), such as convincing help desk services to add unauthorized MFA devices to compromised accounts,” said the FBI alert. “They target large corporations and their third-party IT providers, which means anyone in the airline ecosystem, including trusted vendors and contractors, could be at risk.”
Technical analysis of the Qantas 2025 data breach
From the intelligence Unosecur aggregated and analysed, this is the tentative path of the Qantas 2025 data breach.

Qantas 2025 data breach: root cause and breach vector
Primary attack vector: The breach originated from the exploitation of a vulnerable public-facing API tied to a third-party customer service platform used by a Qantas offshore contact centre (reportedly based in Manila).
Nature of the vulnerability: Attackers gained unauthorized access by exploiting this API, enabling systematic retrieval of customer data, a method mapped to T1190 (Exploit Public-Facing Application) from the MITRE ATT&CK framework. Further indicators suggest that weak third-party access controls and insufficient identity verification were contributing factors.
Potential supplementary methods
Social engineering/impersonation: Many experts and threat intelligence sources attribute the attack to the Scattered Spider cybercriminal group, which is known for advanced social engineering against help desks and vendor platforms.
Impersonation and phishing: Inferred use of spearphishing and impersonation to collect or abuse valid credentials, mapped to MITRE tactic T1566.002 (Phishing: Spearphishing Link) and T1078.004 (Valid Accounts: Cloud Accounts).
Data compromised and attack impact
Exposed data fields:
- Names
- Email addresses
- Qantas Frequent Flyer numbers (and sometimes tier/status/points)
- Addresses (residential, business, hotel delivery)
- Dates of birth
- Phone numbers (mobile/landline/business)
- Gender and meal preferences
Data safety assurance: No credit card data, financial details, passport information, or account passwords/PINs were stored on or stolen from the compromised system.
Forensic confirmation: The attack did not grant access to the main Qantas IT infrastructure or operational flight systems—impact remained limited to customer records on the third-party platform.
Defensive and containment actions
Containment: The affected system was taken offline and isolated; immediate restrictions were placed on all remote and vendor connections.
Legal and monitoring: Qantas secured a Supreme Court injunction to restrict stolen data usage/distribution. Enhanced monitoring and threat intelligence feeds were deployed to track potential misuse or sale of the data.
Security improvements: Tightened access controls and identity verification for all help desk and partner systems. Accelerated patching and configuration review of all customer-facing APIs and interfaces
(H5) PII exposure, legal action, and reputation: Business impact for Qantas and peers
All of these boils down to one crucial factor: third-party risk is a critical vulnerability.
- The breach did not occur through Qantas’ own internal systems; it was made possible by exploiting a third-party call centre platform that held customer data for millions.
- Attackers took advantage of vulnerabilities in an external provider—specifically, either exploiting a vulnerable API or by leveraging methods like social engineering or credential theft often used by groups such as Scattered Spider.
- The Qantas 2025 data breach reveals that robust internal defenses and compliance are not enough; supply chain/vendor risk must be recognized as part of an organization’s own attack surface.
- Serious security questions surround third-party risk management, with sophisticated groups increasingly relying on indirect pathways such as vendors, help desks.
As we often reiterate to our clients, cybersecurity is no longer a tech issue. It’s a is a core business, reputation, and operational risk, much beyond IT.
- The Qantas 2025 data breach resulted in the exposure of sensitive information of 5.7–6 million customers; this scale of breach poses not just IT risks but also reputational, regulatory, and legal threats to the company.
- Qantas’ core business operations were not impacted, but the brand trust and customer confidence suffered significant harm, requiring crisis communication, legal notification, and support lines for affected customers.
- The breach demonstrates that regulatory compliance alone (“checkbox security”) does not guarantee resilience. Business leaders must treat cyber risk, including that arising from digital supply chains, as a board-level issue with consequences across the whole organization.
- Compliance doesn’t always mean protection and resilience. The Qantas 2025 data breach underscore the necessity for executive-level security strategy and vendor oversight.
Tech companies with wings
Airlines, and the companies that support them, are essentially tech firms that happen to take flight. Because their operations are digital at their core, security has to be woven into every workflow and partnership from the outset rather than tacked on later. Aviation businesses must treat their vendors as part of their own attack surface and continuously invest in both technological defenses and human awareness across the extended enterprise. Reputational damage, regulatory scrutiny, potential customer litigation, and operational disruption can result from incidents originating outside direct organizational control.
Sector business leaders must recognize and act upon the fact that cyber risk is existential, requiring integrated, strategic management across functions and partners
Don’t let hidden identities cost you millions
Discover and lock down human & NHI risks at scale—powered by AI, zero breaches.