Zero Trust identity security: Framework, five-step roadmap, and metrics
.png)
The Unosecur engineering and product teams have consulted several partner firms on their security posture. We have seen many Zero Trust initiatives fail because they focus on tools instead of identities.
Zero Trust identity security — TL;DR
What is Zero Trust identity security?
Verifying every identity in real time, minimizing access rights (least privilege), and automating threat detection and mitigation.
Why does Zero Trust identity security matter?
It delivers a resilient, identity‑first security posture that withstands modern threats better than tool‑centric approaches.
How should an organization proceed in setting up identity-focused Zero Trust security?
Follow a five‑step roadmap, track essential metrics, and avoid common pitfalls to move beyond stalled projects and achieve durable Zero Trust outcomes.
What does Zero Trust identity security mean?
Attackers often bypass firewalls by signing in with valid credentials. Zero Trust Identity Security reverses this approach by starting with continuous verification of every human and machine identity, then minimizing what each can do, and automating detection and remediation when behavior changes.
Zero Trust Security operates on the principle of "never trust, always verify." Applying this to identity means that every access request must meet three key requirements simultaneously:
- Strong authentication: Proof of identity using multifactor authentication (MFA) or passwordless methods.
- Least privilege authorization: Grant users and machines only the permissions they currently need.
- Continuous evaluation: Every action is assessed in real time against context (such as user role, device status, session risk, and location).
Unlike traditional one-time logins granting broad network access, each access request here is dynamically scrutinized, making it much harder for attackers to move laterally within your network.
What are the core principles of Zero Trust identity security?
- Assume breach: Treat every network segment and identity endpoint as potentially compromised.
- Verify explicitly: Employ MFA/passwordless techniques and factor in device posture and risk signals before allowing access.
- Least privilege: Assign entitlements with Just-in-Time elevation where possible, ensuring that users and machines have only the minimum necessary permissions at any given time.
- Continuous monitoring: Detect anomalous activity in sessions, tokens, and machine identities throughout their lifecycle.
- Automated response: Respond instantly to identity threats by revoking access, rotating credentials, or disabling accounts without manual delays.
How do we implement Zero Trust identity security?
Here is a five-step broad roadmap to implement Zero Trust identity security
1. Inventory and visibility
- Catalogue all identities: human users, service accounts, API keys, roles, groups.
- Map effective permissions across cloud and on-premises directories.
- Normalize identity data into a consolidated, single pane of glass.
Why: Without inventory and visibility, your Zero Trust identity security program cannot effectively control or verify identity access, severely weakening your overall security posture and increasing the risk of costly intrusions.
2. Strengthen authentication (MFA + passwordless)
- Prioritize near-total MFA for privileged and administrative accounts.
- Expand MFA coverage to all users system-wide.
- Introduce passwordless authentication methods (e.g., FIDO2, platform authenticators).
Why? Because it forms the primary barrier preventing attackers from exploiting stolen or weak credentials, thus securing critical access points in a Zero Trust environment while enhancing user convenience and compliance.
3. Adaptive access and least privilege
- Replace broad static roles with dynamic policies factoring in device health, geographic location, session risk, and behavioral context.
- Implement Just-in-Time privilege elevation for sensitive admin tasks.
- Regularly review and remediate excessive permissions through Cloud Infrastructure Entitlement Management (CIEM) and Identity Governance and Administration (IGA).
Why? They are required to enforce precise, risk-aware, and time-bound access controls, reducing the risk of breaches from compromised or misused credentials and ensuring your environment remains tightly secured against evolving threats.
4. Continuous monitoring (Identity Threat Detection and Response - ITDR)
- Monitor authentication flows, token issuance, directory changes, and machine identity usage in real time.
- Detect anomalies such as sudden permission escalations, logins from unusual geolocations, and unexpected activation of dormant service accounts.
- Track excessive failed MFA attempts indicating possible brute force or credential stuffing attacks.
Why? Without continuous monitoring, you’re essentially flying blind, letting attackers exploit stolen or misused credentials and elevated permissions without being detected quickly.
5. Automation & Metrics
- Automate remediation actions: disabling compromised accounts, rotating secrets, revoking tokens, triggering step-up authentication.
- Surface actionable metrics to leadership using dashboards.
- Continuously refine policies and response playbooks based on metric trends.
Why? Without automation and metrics, identity security remains slow, reactive, and difficult to measure or improve systematically.
What are the key metrics to track the effectiveness of Zero Trust identity security?
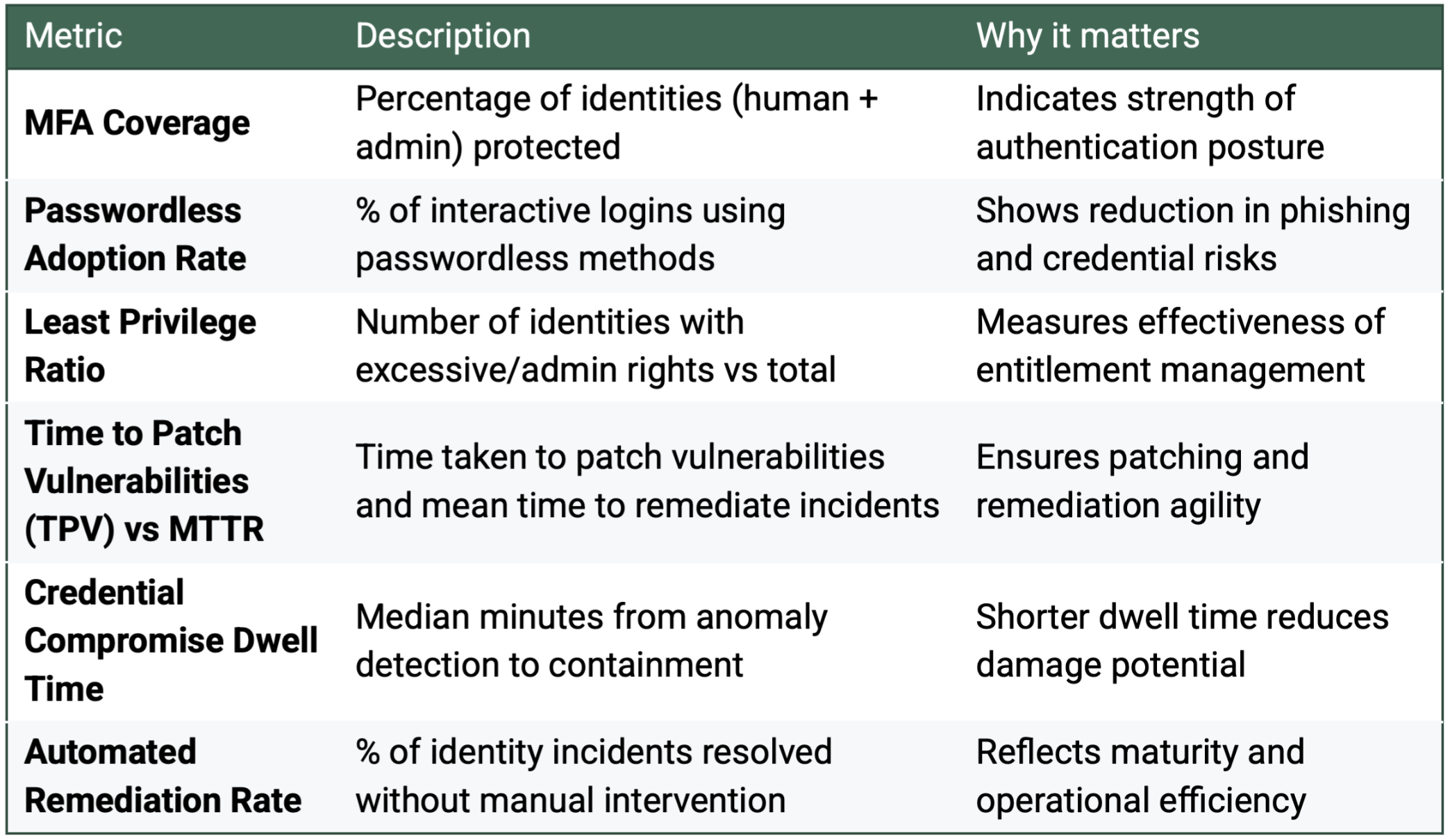
What are the common early pitfalls in Zero Trust identity security?
- Skipping Identity Inventory: Without a clear baseline, you cannot track progress or detect drift.
- Rolling Out MFA Without Managing User Experience: Ignoring user friction can lead to low adoption and shadow workarounds.
- Neglecting Non-Human Identities: Service accounts, API keys, and machine IDs are lucrative targets if left unmanaged.
- Failing to Define KPIs: Without metrics, your Zero Trust program lacks direction and accountability.
Remedy: Treat Zero Trust identity security as an iterative program. Start with visibility, then tighten controls, and finally automate response while continuously measuring success.
Don’t let hidden identities cost you millions
Discover and lock down human & NHI risks at scale—powered by AI, zero breaches.



