2025 Year-End Cloud Identity Attack Case Study
TL;DR
Cloud security incidents in 2025 confirmed one truth: identity is now the primary attack surface. Attackers have moved beyond trying to "break" into the cloud; they are simply using valid, trusted credentials to walk through the front door. This blog breaks down the eight identity patterns defining the modern threat landscape and shows how an identity-first approach, powered by Unosecur, turns these invisible risks into governable outcomes.
The End of the "Front Door" Era. We have spent years perfecting MFA and login portals, but 2025 proved that a successful login is no longer a guarantee of a safe user. Across major incidents this year, attackers consistently relied on legitimate cloud identities, IAM credentials, OAuth tokens, service accounts, and CI/CD identities that cloud platforms already trust.
The access was legitimate, but the misuse was malicious. These actions blended into normal operational behavior, making them nearly impossible for traditional tools to spot. The failure wasn't a broken security tool; it was a failure of unchecked trust. To survive in this environment, security teams must move from "protecting the login" to "governing the identity lifecycle."
Identity Attack Patterns Observed in 2025
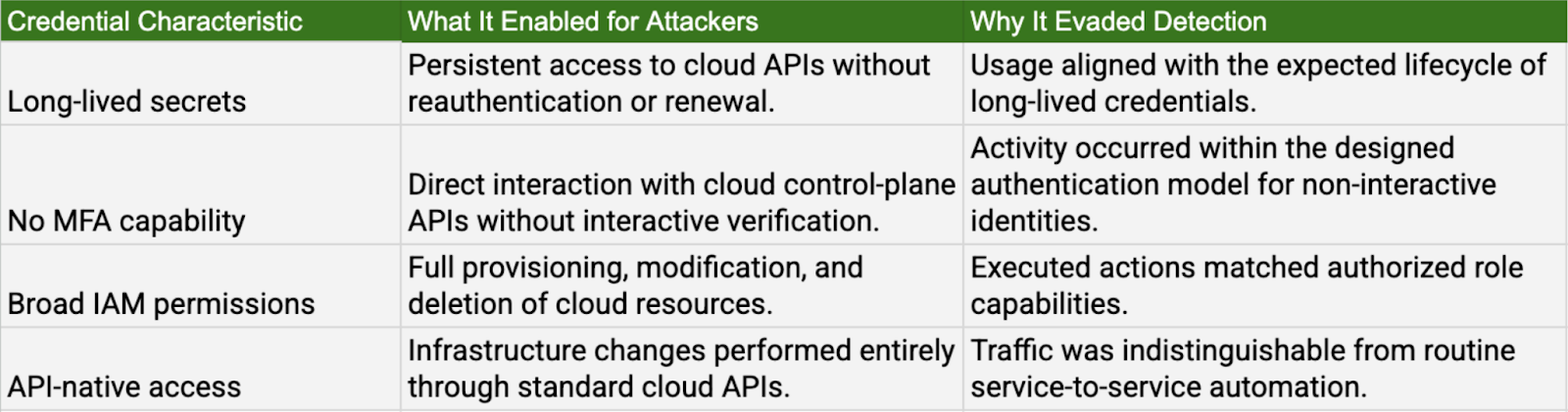
Pattern 1: Static cloud credentials used as direct cloud entry
Observed incidents: DeepSeek AI, Tata Motors E-Dukaan, Tech Giants Seed DB, Shai-Hulud 2.0, Red Hat Consulting, and AWS cryptojacking via compromised IAM credentials.
Attackers obtained long-lived credentials, such as permanent API keys, SSH keys, and hardcoded secrets, from publicly exposed repositories, databases, or misconfigured storage locations and used them to authenticate directly to cloud APIs. These credentials enabled full interaction with cloud control planes, including infrastructure provisioning and configuration changes, without requiring MFA or interactive authentication.
All activity occurred through identities designed for automation. Cloud audit logs reflected valid API calls performing expected operations, with no anomalous login behavior or authentication failures to distinguish malicious misuse from legitimate service activity.
Why this mattered: Static credentials functioned as permanent cloud identities without effective lifecycle controls.
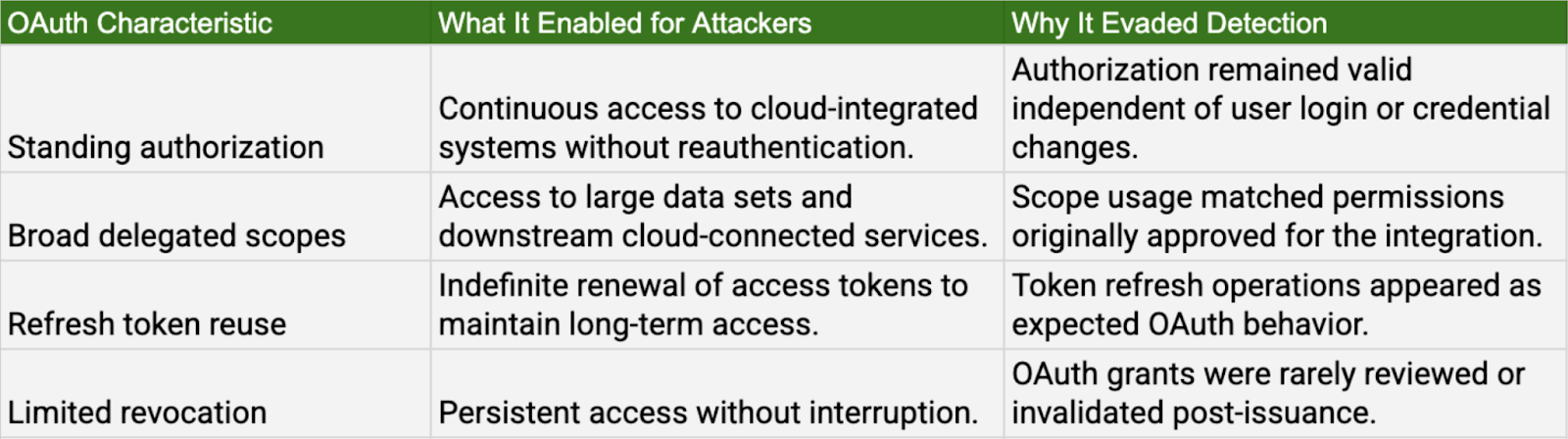
Pattern 2: SaaS OAuth compromise creating persistent cloud access
Observed incidents: Salesloft / Drift OAuth compromise (UNC6395).
Attackers stole OAuth access and refresh tokens issued to a trusted SaaS integration and reused them to access cloud-integrated Salesforce environments. The compromised OAuth grants enabled access without reauthentication or MFA, which allowed continued interaction with downstream cloud-connected systems.
OAuth activity appeared continuous and authorized. Password resets, MFA enforcement, and session invalidation on associated user accounts did not affect the standing OAuth grants, allowing access to persist without generating security signals.
Why this mattered: OAuth grants became durable cloud identities independent of user authentication state.
Pattern 3: CI/CD and developer identities acting as tier-0 cloud access
Observed incidents: Pearson / Internet Archive, Toptal GitHub, Red Hat Consulting, Shai-Hulud 2.0, and React2Shell.
Attackers compromised CI/CD pipelines, repository tokens, and developer tooling identities to obtain cloud credentials and interact directly with cloud control planes. These identities enabled infrastructure deployment, access to secrets, and the assumption of privileged roles without additional authorization.
All actions followed expected automation workflows. Activity executed through pipelines generated no interactive authentication events and blended into routine CI/CD operations already trusted by the environment.
Why this mattered: CI/CD identities concentrated control-plane privilege with minimal identity oversight.

Pattern 4: Abuse of non-human cloud identities
Observed incidents: AWS Bedrock Agents and AWS IAM Shadow Admin.
Attackers abused service accounts and AI agent identities through delegated permissions and role chaining to achieve privileged outcomes. These automated workflow identities enabled administrative actions without requiring explicit administrator role assignment. Operations were performed entirely by non-human identities using assigned permissions. Logs reflected valid service-to-service behavior, with no indicators associated with human misuse or authentication abuse.
Why this mattered: Non-human identities combined high privilege with low visibility and weak governance.

Pattern 5: MFA neutralized through token and session reuse
Observed incidents: DoD Contractors, 16-billion-record Shadow Dump, and Cisco Dev Portal.
Attackers bypassed the multi-factor authentication (MFA) to steal valid sessions and access tokens. Crucially, the system failed to require additional authentication or token revalidation after the initial issuance. This oversight permitted persistent access, allowing the attackers to reuse the tokens for unauthorized actions.
Why this mattered: MFA protected login events but failed to protect post-authentication identity usage.

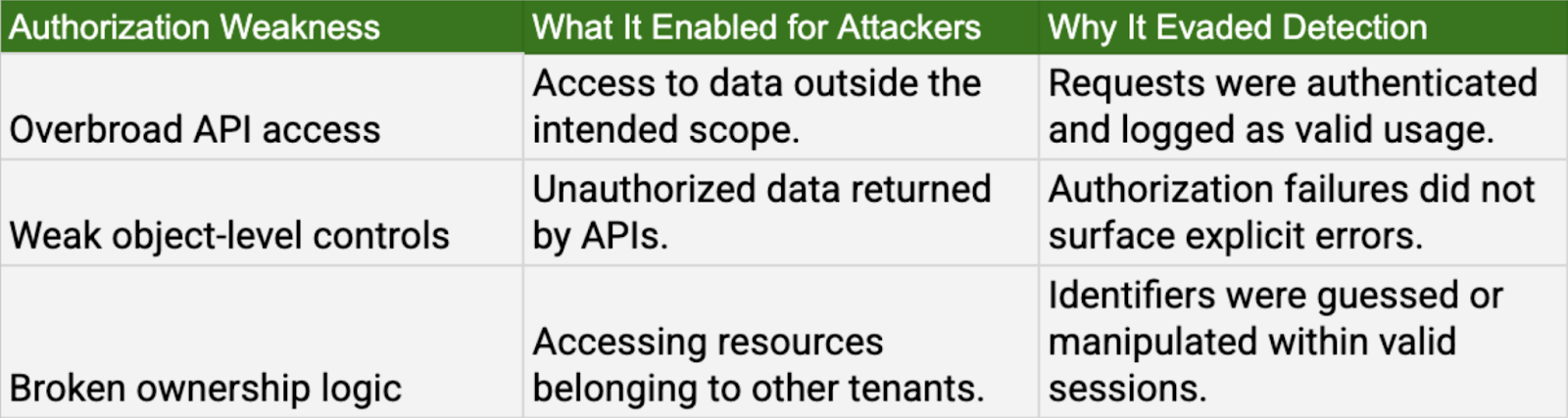
Pattern 6: Authorization failures enabling cross-scope cloud access
Observed incidents: Toyota Telematics and Tata Motors E-Dukaan.
Attackers bypassed authentication with legitimate user identities, then exploited weak object-level authorization to manipulate internal APIs and access data. This breach stemmed from a failure to enforce granular permissions, allowing valid identities to perform operations outside their defined scope.
Why this mattered: Authorization failures allowed legitimate identities to exceed intended access boundaries.
Pattern 7: Identity misconfiguration as the root cause of impact
Observed incidents: DeepSeek AI, Toyota Telematics, and Tata Motors E-Dukaan.
Attackers exploited over-permissive roles and unsafe trust relationships to gain unauthorized access to cloud resources. The critical finding is that this was not a result of a security vulnerability; instead, the access was successful because it fully complied with the existing, albeit poorly configured, permissions within the cloud environment.
Why this mattered: Misconfiguration scaled attacker impact without increasing attacker sophistication.

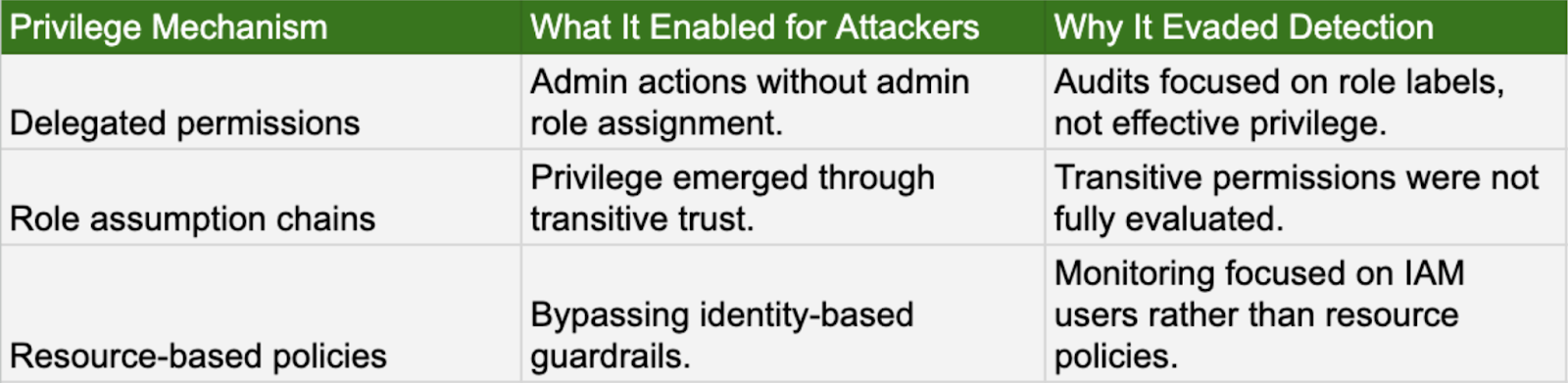
Pattern 8: Privileged outcomes without explicit admin roles
Observed incidents: Azure Entra CVE-2025-55241, AWS IAM Shadow Admin, and AWS Bedrock Agents.
Attackers exploited delegated permissions to execute administrative tasks, bypassing the need for explicit admin role assignments. This emergence of privilege stemmed from established trust relationships within the cloud identity environment. Essentially, the attackers gained administrative capabilities through trust rather than direct role-based access control.
Why this mattered: Privilege existed in relationships rather than declared roles.
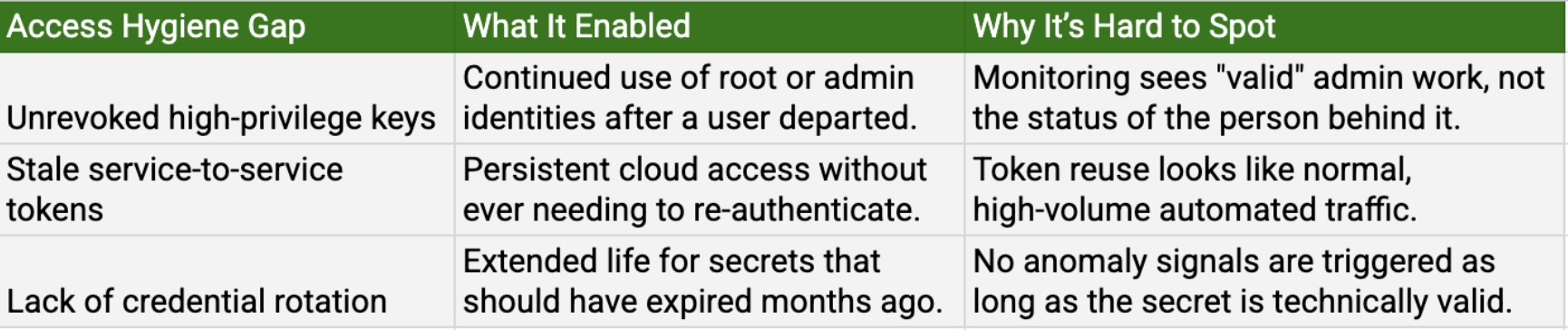
Pattern 9: Improper offboarding and lingering access
Observed incidents: AWS Root Account Compromise, Coupang incident
Often, the biggest threat isn't a hacker breaking in; it's a former employee whose access was never actually cut off. Attackers love hunting for "stale" credentials that should have been killed weeks ago. Since these accounts were already vetted, they don't trigger any red flags when they log back in. They just stay active in the background, turning a simple oversight into a permanent back door.
Why this matters: Lifecycle controls failed. Access that should have been dead stayed live, allowing attackers to hide in plain sight using identities that were "authorized" on paper but dangerous in reality.
Forecast: How cloud identity attacks will evolve
The 2025 incidents reflect structural realities of cloud environments rather than temporary weaknesses. As automation, federation, and decentralized ownership expand, identity will remain the most reliable and least noisy attack surface. Attackers will prioritize durable access over initial compromise, targeting identities that enable long-term operation without reauthentication. These access paths mirror legitimate cloud usage, making them inherently stealthy and difficult to distinguish from normal operations.

Conclusion
The confirmed 2025 incidents demonstrate a consistent reality: cloud compromise now occurs after trust is granted, not before. Identity systems were not broken; they were used exactly as designed, but beyond safe assumptions. Modern cloud defense requires continuous evaluation of identity usage across human, non-human, and federated identities. Authentication alone is insufficient. Identity behavior over time is now the true security boundary.
If you want to understand how Unosecur detects, prevents, and remediates these identity-driven attack paths, this is precisely the problem space it was built to solve.
Don’t let hidden identities cost you millions
Discover and lock down human & NHI risks at scale—powered by AI, zero breaches.



