Why identity-first Zero Trust security trumps traditional perimeter: Lessons for managers

Work no longer happens neatly inside static borders. Identities are everywhere, and attackers know it. Perimeter security alone cannot protect your organization from credential misuse, SaaS breaches, or privilege escalation in the cloud.
Zero Trust flips the security model: trust no one by default, continuously verify everyone and everything by context, and minimize entitlements everywhere.
TL;DR
- Perimeter security is outdated: It assumes everything inside is trusted, leaving blind spots in SaaS, cloud platforms, and over‑provisioned accounts, which attackers exploit for lateral movement.
- Identity-first Zero Trust fixes these gaps: It continuously verifies every access request using risk signals, device health, and entitlements, enforcing least privilege dynamically.
- Better defenses against credential attacks: Passwordless and MFA drastically cut phishing and credential‑stuffing risks, while ITDR detects unusual identity behavior in real time.
- Practical transition steps: Map all identities and apps, enforce MFA/passwordless, apply adaptive policies, review entitlements continuously, and automate identity threat detection/response.
- Progress metrics matter: Track MFA coverage, privilege reduction, MTTR for credential incidents, and declining VPN reliance to measure maturity toward Zero Trust resilience.
Case in point: Why is traditional security perimeter outdated?
In May 2025, hackers exploited an unknown flaw (CVE‑2025‑3928) in Commvault Metallic, a cloud backup service hosted on Microsoft Azure.
By planting malicious code through this vulnerability, they gained access to application secrets and tokens used to connect Commvault’s system with customer Microsoft 365 accounts.
Although backup data itself wasn’t confirmed stolen, these stolen tokens could let attackers impersonate customers and move into their Microsoft 365 environments.
Like many other attacks, what happened at Commvault proves that the traditional security perimeter fails to prevent present-day attacks:
- Cloud SaaS environment: The attack targeted Commvault’s Metallic SaaS backup service, which operates in Azure, outside traditional enterprise network perimeters.
- Credential misuse risk: The exploited vulnerability (CVE‑2025‑3928) exposed application secrets and OAuth tokens used for Microsoft 365 integrations. This allowed potential privilege escalation inside customer cloud environments, bypassing perimeter defenses.
- No direct network breach: There was no compromise of Commvault customers’ internal firewalls or on‑prem systems; the attack was entirely focused on cloud identity and SaaS trust relationships.
- Lateral movement via identities: Even though backup data wasn’t directly stolen, compromised service accounts could have allowed attackers to impersonate customers and gain elevated privileges in their Microsoft 365 tenants.
In identity security, what are the limitations of the traditional perimeter model?
1. Implicit trust leads to lateral movement
Perimeter security trusts everything inside the network. Once an attacker breaches the perimeter - via phishing, VPN compromise, or malware - they can move laterally with minimal detection, accessing sensitive systems and data.
2. Invisibility to cloud and SaaS activities
Traditional firewalls and VPNs cannot monitor or enforce access policies within external SaaS providers or cloud platforms. Identity-based access in platforms like Microsoft 365, Salesforce, or AWS is invisible to perimeter controls, leaving major blind spots.
3. Credential vulnerabilities
Relying solely on usernames, passwords, and basic VPNs exposes organizations to phishing, password reuse, and credential stuffing. Attackers can compromise an account outside the network and gain full access once inside.
4. Over-provisioned accounts and static roles
In perimeter models, user entitlements are rarely reviewed and accumulate excessive permissions over time. Network segmentation is often unable to adequately compensate for unnecessary access within applications and clouds.
What are the advantages of identity-first Zero Trust security over traditional perimeter networks?
1. Granular, contextual access decisions
Zero Trust evaluates every access request using dynamic policies that consider user risk signals, device health, location, and entitlements, regardless of where the user is connecting from.
2. Continuous least privilege enforcement
Integrated CIEM (Cloud Infrastructure Entitlement Management) and IGA (Identity Governance and Administration) tools regularly review and right-size permissions for every identity, minimizing the attack surface and privilege misuse.
3. Continuous monitoring with ITDR
Identity Threat Detection and Response (ITDR) establishes behavioral baselines for every identity, flagging sudden privilege escalations, unusual token activity, or access attempts from unexpected locations—no matter the network.
4. Enhanced resilience against phishing and credential attacks
By requiring passwordless authentication (e.g., biometrics or FIDO2) and enforcing MFA, Zero Trust drastically reduces the risk of credential-based attacks. Adaptive access blocks or limits sessions that show risky behavior.
5. Agility in a distributed world
Zero Trust is designed for remote workforces, contractors, cloud-native apps, and machine identities, making security frictionless, scalable, and relevant wherever work happens.
What are the practical steps to transition from traditional perimeter to Zero Trust?
1. Assess your environment
- Inventory and map all applications (cloud and on-prem).
- Catalogue identities, with special attention to privileged and non-human (machine, API) accounts.
Why? You can’t protect what you don’t know exists. By inventorying all applications (cloud and on-prem), and cataloguing identities, especially privileged and machine accounts, you build visibility into your attack surface.
2. Harden authentication
- Achieve full MFA and passwordless adoption, starting with high-risk, administrative users.
Why? Implementing Multi-Factor Authentication (MFA) and passwordless technologies makes credential theft, phishing, and brute-force attacks far less effective, especially for privileged accounts, a prime target for attackers.
3. Introduce adaptive access policies
- Implement risk-based controls (e.g., step-up authentication for suspicious logins, geo-location changes, or device health failures).
Why? By evaluating each access attempt in context (user/device risk, geo-location, session anomalies), you can step up authentication or block risky sessions immediately.
4. Reduce and continuously review entitlements
- Apply least privilege principles; use Just-in-Time privilege elevation for sensitive actions.
- Remediate over-privileged and dormant accounts, especially in the cloud.
Why? Excessive or lingering privileges are a prime target for attackers post-breach. Applying least privilege and Just-in-Time elevation means elevated access is only granted exactly when needed and for the minimum time.
5. Automate detection and response
- Deploy ITDR solutions to monitor identity risks in real time.
- Automate responses: revoke compromised tokens, rotate secrets, or disable risky accounts with minimal manual intervention.
Why? ITDR (Identity Threat Detection & Response) lets you catch attacks as they happen, not weeks or months later. This shortens attacker dwell time and limits damage.
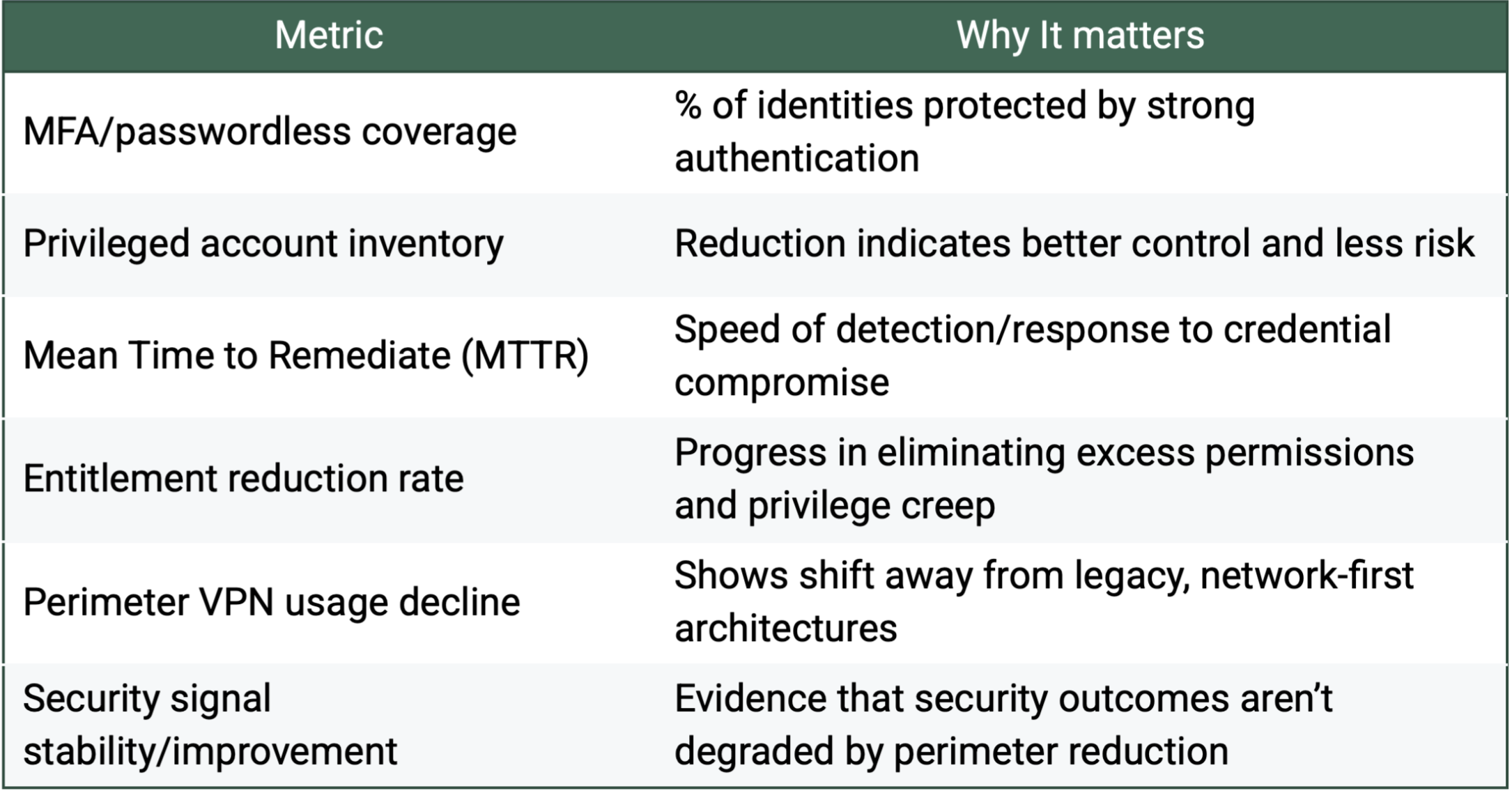
What are the Identity metrics for measuring the progress of transition to Zero Trust?
Tracking these key identity-centric metrics shows how far your organization has moved from perimeter risk to Zero Trust resilience:
What should be your next step?
Start by understanding where identities live and what they can access. Deploy strong, adaptive authentication. Tighten permissions continuously. Monitor all identity activity, then automate your response.
Organizations that learn these identity lessons and outgrow their perimeters will be the ones best equipped for next-generation cyber threats.
Don’t let hidden identities cost you millions
Discover and lock down human & NHI risks at scale—powered by AI, zero breaches.



