The New Frontier of Identity Security: Governing Agentic AI and MCP with Unosecur
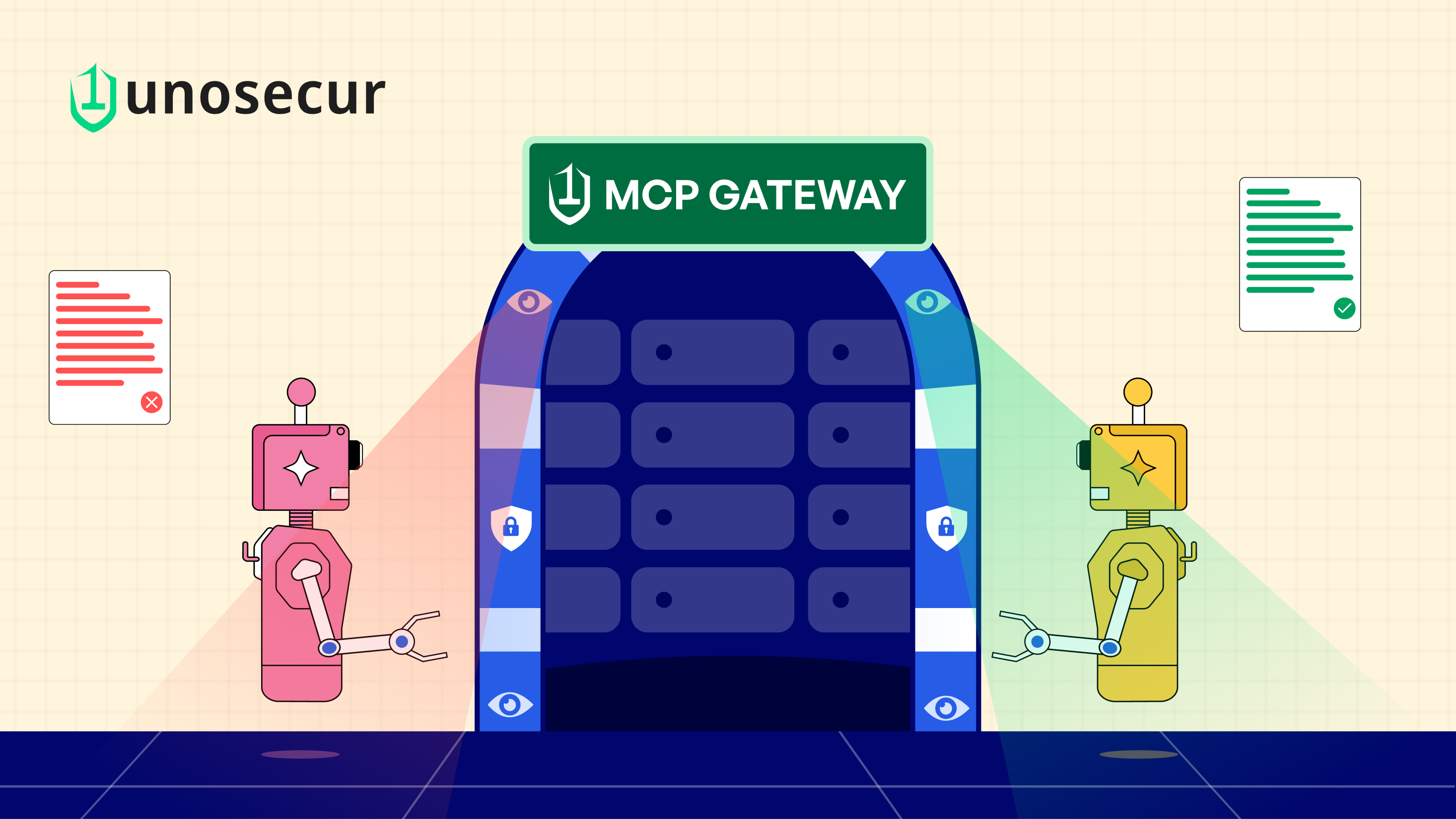
As we covered in previous posts, AI systems are no longer limited to generative conversations or analysis. They are now agentic: capable of selecting tools, invoking APIs, accessing live data, and executing multi-step workflows autonomously. Model Context Protocol (MCP) has emerged as the connective tissue enabling this shift. If you want a detailed breakdown of what MCP is and how it works, we’ve covered that separately. This piece focuses on what matters next: Why MCP creates a new identity security problem in production and what it takes to govern it.
From capability to risk: When Agentic AI meets reality
MCP is rapidly becoming the foundational infrastructure for enterprise AI. All major model providers support it. Thousands of MCP servers now exist, spanning databases, SaaS platforms, internal tools, and developer workflows. Software vendors are shipping official MCP servers, and enterprises are deploying custom ones at speed. But this adoption curve has exposed a hard truth: MCP expands identity faster than security teams can see or govern it.
In most environments today, AI clients connect directly to MCP servers with little to no centralized control. Each connection introduces new credentials, new trust assumptions, and new execution paths. Over time, this creates what many teams are now experiencing firsthand: unchecked MCP sprawl.
The core challenge: MCP sprawl and systemic identity risk
The security issue with MCP is not theoretical. Large-scale research across thousands of MCP server implementations reveals deep, structural weaknesses in how identity is handled.
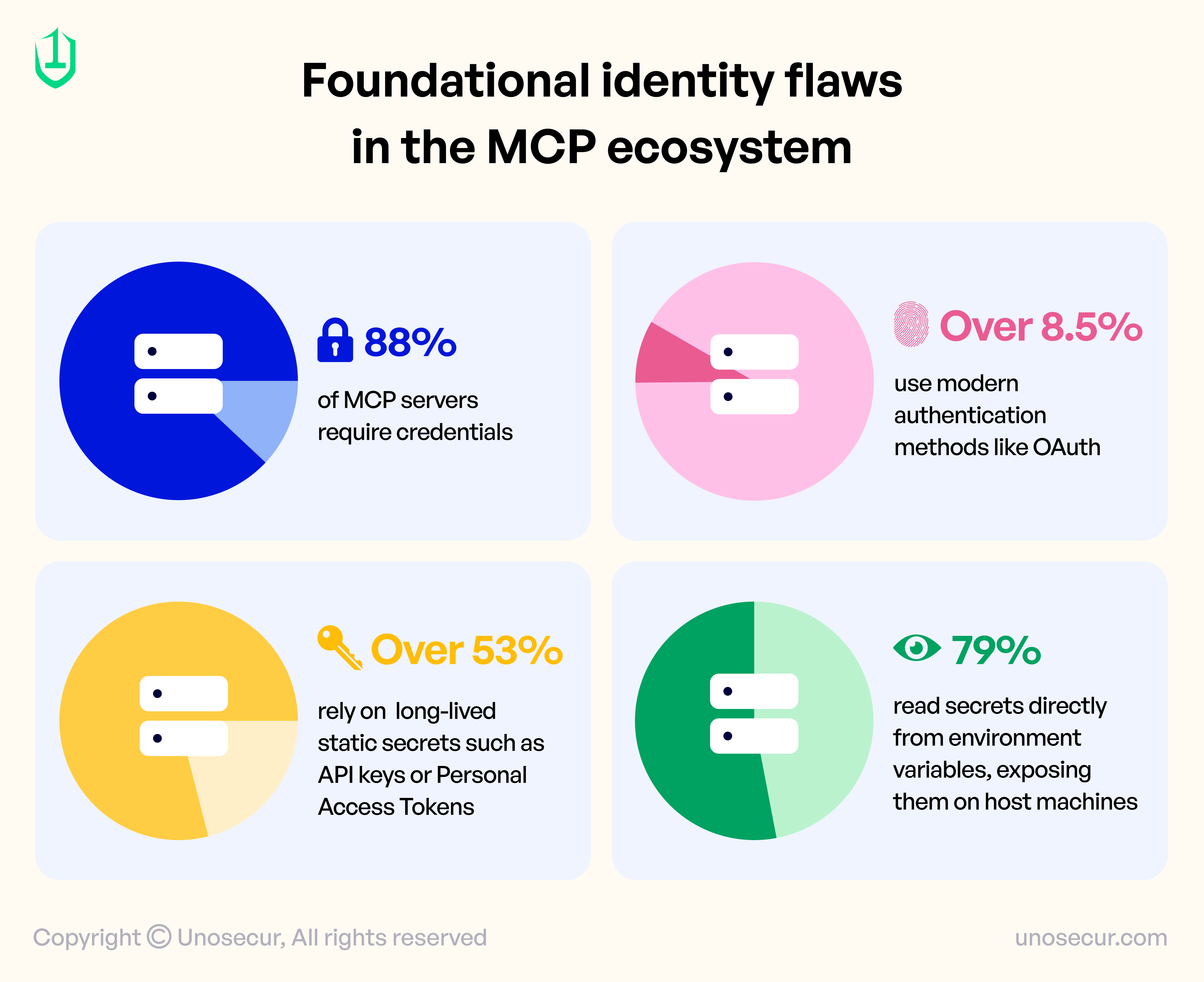
These are not edge cases. They represent the dominant pattern. This means enterprises adopting MCP are inheriting an identity model built on:
- Persistent credentials
- Weak rotation practices
- Minimal auditability
- No centralized enforcement
Traditional IAM systems were never designed for this scale or behavior profile of non-human identities.
The “Lethal Trifecta” that enables new attacks
Security researchers have identified a dangerous convergence in agentic AI systems, often referred to as the lethal trifecta:
- Access to private data
Source code, configuration files, credentials, internal APIs - Exposure to untrusted content
Documentation, web results, API responses, third-party data - Ability to act externally
Making API calls, modifying systems ,and sending data outward
When combined, these capabilities create entirely new attack paths. An attacker no longer needs to break authentication or target stealing high-value credentials. Instead, they can embed malicious instructions inside a content source that an agent already trusts. The agent then uses its legitimate access to execute those instructions.
This has led to real-world attack patterns that traditional security tooling cannot detect:
- Prompt injection through tools, where malicious instructions live inside tool descriptions
- Tool poisoning, where seemingly legitimate MCP servers perform hidden actions
- Agent-driven secret discovery, where agents autonomously locate and exfiltrate credentials from .env files, keychains, or SSH config
Every action is technically allowed. That is what makes these attacks so difficult to detect.
Governance and compliance blind spots
Beyond direct exploitation, MCP sprawl introduces glaring governance gaps:
- No centralized visibility into which MCP servers are configured or trusted
- No consistent logging of agent actions across tools
- No chain of custody for who accessed what, when, and why
For regulated environments, this creates immediate exposure. Compliance frameworks such as SOC 2, HIPAA, and FINRA require traceability, auditability, and control. MCP, in its default form, provides none of these.
The Unosecur solution: Governing Agentic AI through identity
Unosecur addresses MCP risk by treating agentic AI for what it truly is:
An identity expansion event.
Rather than bolting controls onto tools or models, Unosecur extends identity security principles to cover AI agents, MCP clients, and MCP servers as first-class entities. The result is unified governance across:
- Human identities
- Non-human identities
- AI agents
- MCP tools and servers
All enforced consistently across cloud, SaaS, on-prem, and hybrid environments.
Announcing the Unosecur secure MCP Gateway
To directly address the governance gaps of MCP and Agentic AI, Unosecur now provides a secure, identity-centric MCP Gateway module, extending our Unified Identity Fabric platform for this new breed of non-human identities. This offering serves as a centralized IAM entry point for all MCP traffic, transforming the standard insecure configuration into a fully governed and observable architecture.
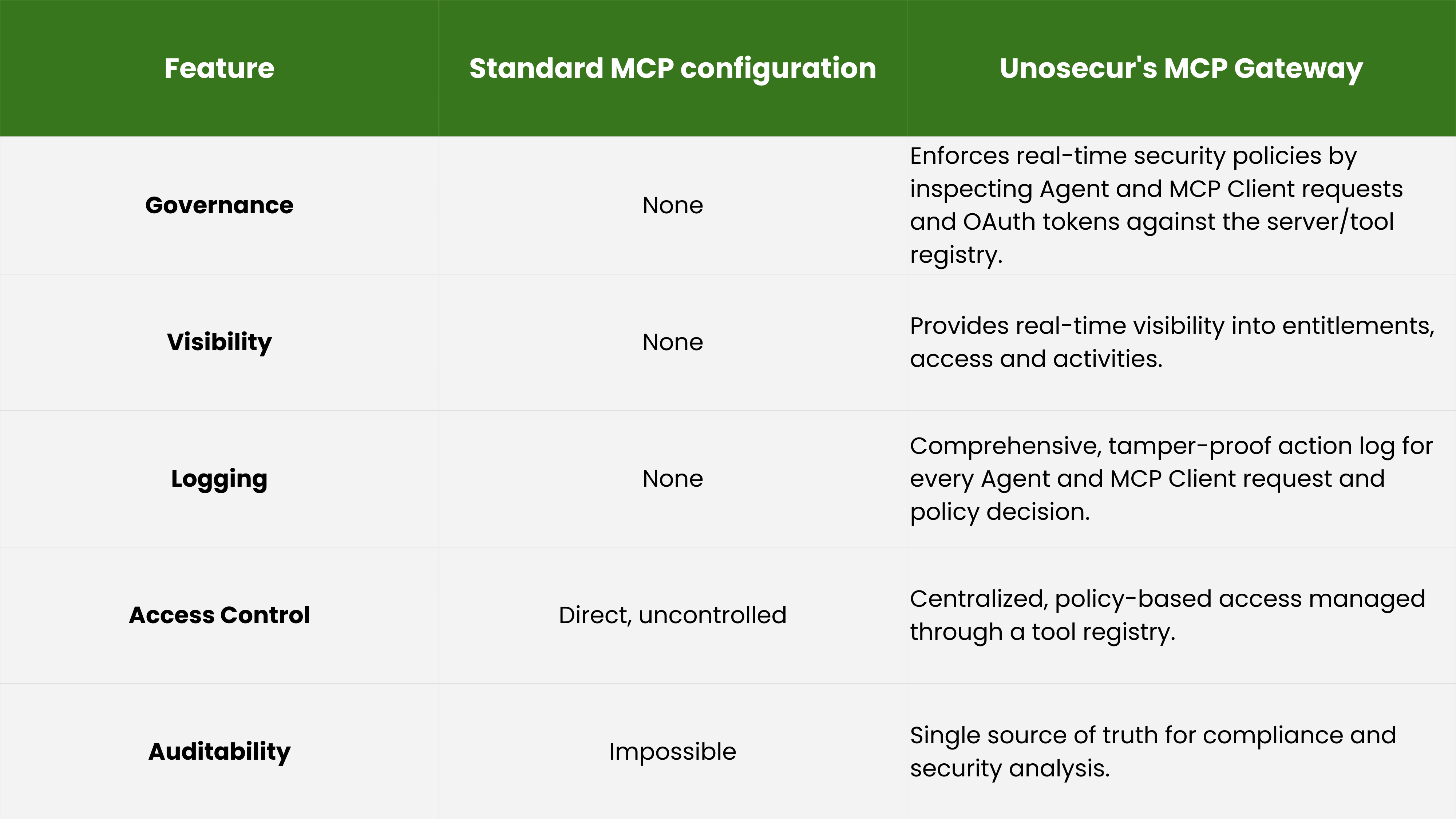
Our gateway is standards-based (MCP, OAuth), highly scalable, and built for security, managing authentication, authorization, session management, and key governance operations.
Key features of the secure MCP Gateway
The gateway empowers security leaders with granular control over AI agent and human access to tools:
- Session & Token Tracking: Monitors all sessions, authentication flows, token usage, and tool calls.
- Policy Manager: Enables activity- and task-based access control, moving beyond static roles.
- Just-in-Time (JIT) Access: Creates time-based policies for MCP tool access, ensuring permissions don’t live forever by default.
- Just Enough Privilege (JEP): Rightsizes permissions for agents, reducing standing access and shrinking the identity attack surface.
The benefits are clear: secure identity management, enterprise-grade governance, zero developer friction, and a model- and toolchain-agnostic solution that ensures secure MCP scalability.
An identity platform born in the AI era
The unique characteristics of autonomous AI agents render traditional IAM and basic NHI systems inadequate. Agentic AI requires a purpose-built identity platform that can manage complex relationships and keep up with the unprecedented speed and scale of agents.
.png)
Unosecur's Agentic identity module and MCP gateway is designed for this new reality, providing the sophisticated, task-driven, and just-in-time controls necessary to govern the next generation of digital identities. By mitigating key threats outlined in the OWASP Agentic Threat Model (Tool Misuse, Privilege Compromise, and Identity Spoofing), Unosecur provides the foundational security needed to innovate with confidence.
Click here to find out more about Unosecur's MCP gateway.
Don’t let hidden identities cost you millions
Discover and lock down human & NHI risks at scale—powered by AI, zero breaches.


.png)